Today I’ll be looking at the Proxmox firewall and what to do about container and VM firewalls. Out of the box Proxmox comes with a firewall installed but not activated. At a minimum you should probably activate the Proxmox firewall for the cluster but it’s up to you how you protect the containers and VM’s
Activating the Proxmox Firewall
If you click the Datacenter node under Server View you’ll see a Firewall option in the Datacentre menu.
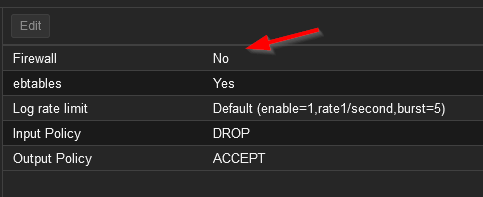
If you select Options you’ll notice that the firewall is current switched off
Before you read what’s below I need to point out that Proxmox has a number of default firewall rules that aim to avoid an accidental lockout issue. For example, if you are on the same local network you should be able to access the web interface and SSH even if you just enable the firewall without making any changes. These default rules don’t show up in the interface. The existing rules can be viewed with iptables-save although I have to admit the output is hard to read. The defaults can be overridden with explicit rules. See here.
Don’t do this right now, but to enable the firewall simply double click that setting and check the box that opens. I say don’t do it now because the default incoming policy, the input policy, is set to DROP. Turning the firewall on now may result in the machine becoming inaccessible for you. We’ll fix that in a moment. Before that though, under the data centre, select your actual server and notice that it too has a firewall setting and it’s own set of options. Additionally, notice that the firewall is switched on in those options but you can access the machine. What gives?
For data centres and servers the firewall settings cascade, if you allow something at the data centre level it will be allowed on the servers. If the firewall is turned off at the data centre level it’s off at the server level which explains why you can access the server. If you look at a container or VM you’ll notice they also have a Proxmox proved firewall. You might expect that server and data centre rules would cascade down but they don’t, at the container and VM level the firewall settings are for that machine only.
To enable the data centre level firewall you need to add just one rule which allows access to the web interface. Select the Datacentre and then Firewall and click Add at the top of the page. Add a rule with the settings: Direction=in, Action=Accept, Interface=vmbr0, Enable=yes, Protocol=tcp, Destination Port=8006 – this will allow anyone to have access to the Proxmox web interface. If your Proxmox is Internet accessible you’ll probably want to limit the source IP’s that can access to the web interface.
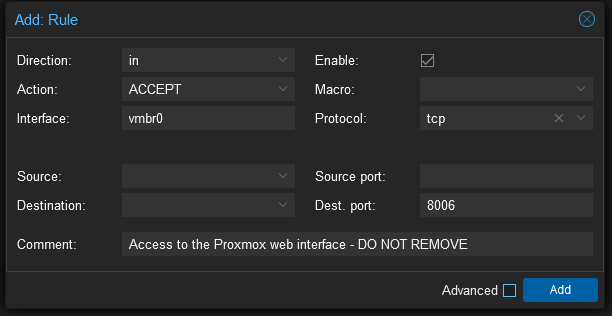
Now got to Datacenter > Firewall > Options and change the Firewall setting from No to Yes. If you’ve configured the rule correctly you should still have access to the web interface but you’ll no longer be able to SSH into the machine so that’s the next thing to fix.
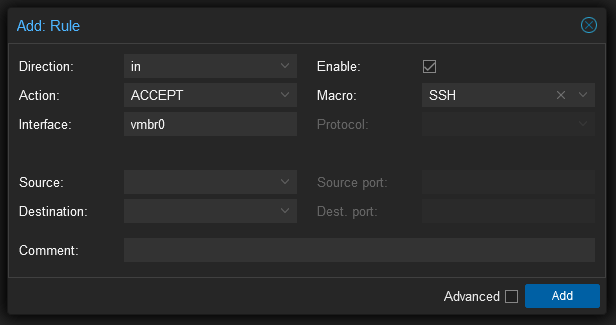
This time we want to access SSH which is a service that has a known port and protocol so rather than specifying them we can select SSH under the macro setting. Again, I’m not specifying a restricted source list here but you probably should if you’re machine is option to the internet. On that front, you should probably arrange is so that people wanting access have to VPN into the local network before they get access to the Proxmox server, that way you can limit access to just a small range of non-routable IP’s.
That should be enough set up for the Proxmox cluster, they really don’t need much incoming access.
Firewalls for Virtual Machines and Containers
There’s a bit of a debate over whether the Proxmox firewall should be used for VM’s and containers or whether they should handle their own firewall needs. Since most of the VM’s and containers you’ll be running are Linux based they all have access to essentially the same firewall that Proxmox is running anyway. Personally, I’m in favour of using the Proxmox provided firewall for guests. Using the Proxmox firewall means you can set up security groups that can be applied to multiple guests quickly e.g. you can create a “default-linux” group that assigns SSH access to all Linux based guests. Similarly you can create address aliases and IP sets that can be used everywhere. Another compelling reason to use the Proxmox firewall is it provides some additional security. If you filter the outgoing traffic of a guest and it becomes compromised the attacker can’t change the outgoing rules without compromising the host as well. If that wasn’t enough, the Proxmox firewall interface is actually pretty good.
Setting up a Security Group
I want all my Linux based guests to have SSH so they all need to port 22 open. I could go though and set a rule for each guest but a much neat way is to create a security group and then assign that group to each guest. Start by selecting Datacenter > Firewall > Security Group and click Create at the top of the page. Enter a name of linux-base and a description if you would like..
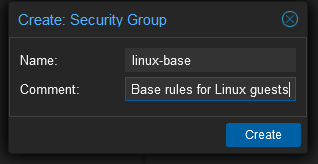
Click the new group and then click Add towards the top of the page to create a new rule for this group. This is just the same SSH rule as we had before with the same caveats about public access.
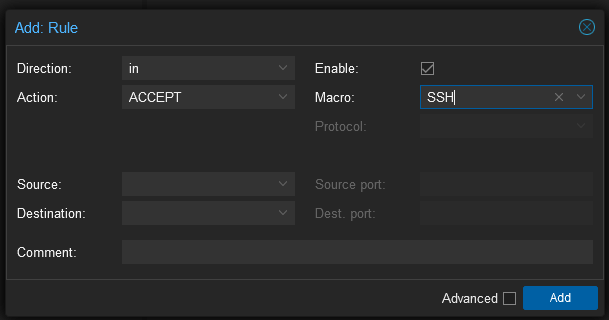
Now select a guest in the Server View and then within the guest select Firewall. Click the Insert Security Group, select the security group and net0 as the interface and tick enable. The interface name tripped me up the first time as I thought it would be vmbr0 but this is the host interface. The security group needs to be applied to the guest interface the name of which can be found under the Hardware settings of the guest – the first interface is usually called net0 though.
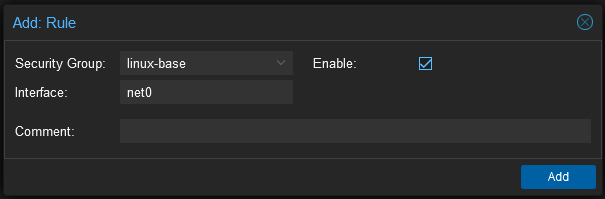
Now select Firewall > Options in the guest and turn the firewall on. You should be able to SSH into the guest but all other access should be blocked. Note that the new rules can take a moment to be applied. The firewall daemon is set to run every ten seconds but it sometimes feels like it takes longer than that to apply rules (maybe I’m just impatient)
Other Firewall Rules and Settings
Depending on what guests you have and what software they are running other groups may or may not be useful but you’ll almost certainly want to set up some individual rules for specific guests. This is carried out in the same way as it is for the host so there’s no point in repeating that again here just remember you need to set the interface to net0.
Something you might like to do is turn on firewall logging, or at least you should know it can be turned on. Under Firewall > Options you can turn on input and output logging separately. By default they are set to nolog, so switch inbound logging to info and look at Firewall > Log as you try to make a connection to the guest on a blocked port.
Enabling Samba
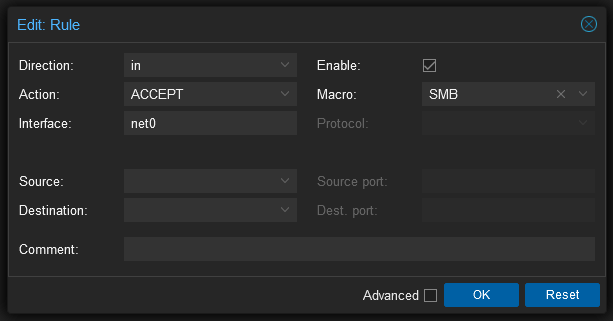
Allowing Samba through the firewall can be a little more trick than other services. I found an excellent post on it here but I found that just the following rule seems to work on Proxmox 8, at least for Windows clients.
Conclusion
That’s all there is to it. The firewall system provided by Proxmox is really first rate and super easy to set up.